4. Be alerted
Immediately receive alerts and trigger actions when something interesting or unusual happens.
Introduction
An alert is always based on a stream. Set up streams that categorize and group messages so you can later alert on aggregated metrics. Streams could be Failed SSH logins, HTTP 500's, blocked ICMP packages or All HTTP requests (to measure response time). Learn more about streams in the documentation.
You can define conditions that trigger alerts. Example: Whenever the stream All production exceptions has more than 50 messages per minute or when the field milliseconds had a too high standard deviation in the last five minutes.
You reach the alert configuration for a stream through the alerts overview page:
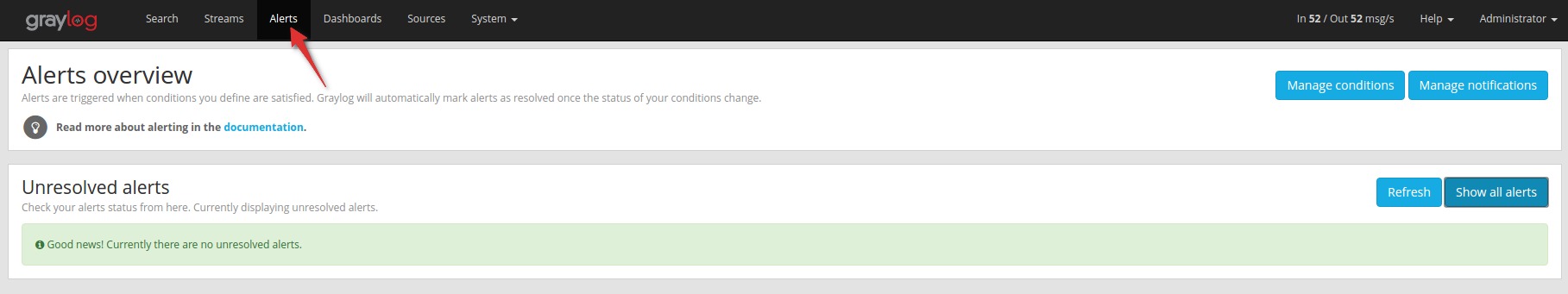
Defining alert conditions
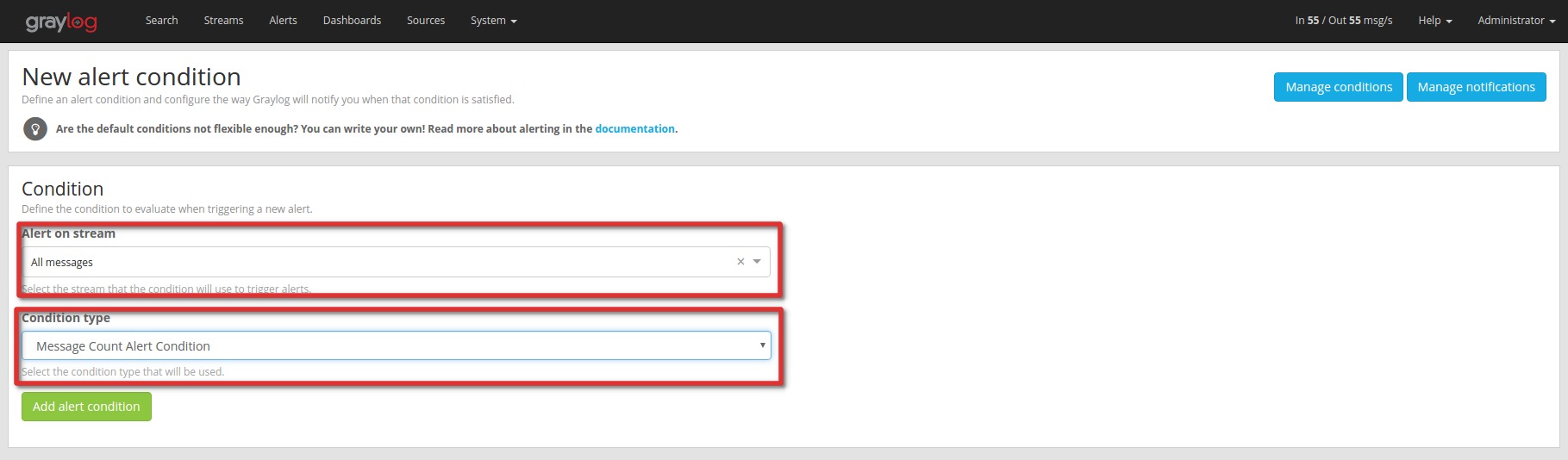
First, you need to create an alert condition to tell Graylog what you consider a situation in which to trigger an alert. Click the Manage conditions button to go to the alert condition management page. On that page hit the Add new condition button and select the stream for which you want to create the condition as well as the condition type.
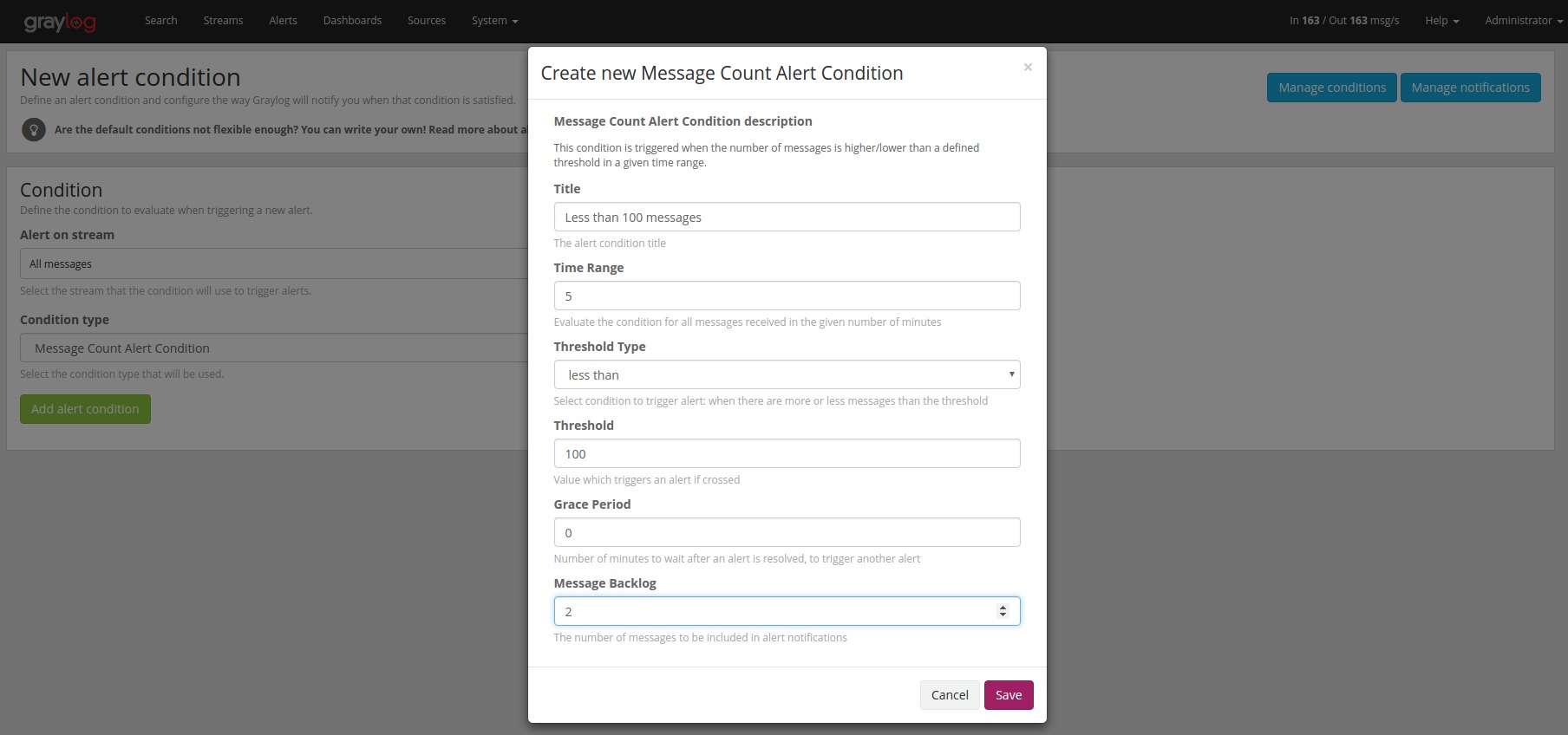
Fill out the form that will be presented to you, and
save the new condition. Graylog will now check every 60 seconds (you can change that interval in
your graylog-server.conf) if any alert condition is triggered, and then send the alerts
you configure on the same page.
The alerts documentation has more details and some use cases. We recommend that you head over there to learn more.